In the evolving landscape of API-driven architectures, Azure API Management (APIM) has emerged as a critical tool for securing, scaling, and streamlining API interactions. At its core, APIM policies empower developers to manipulate requests and responses across the API lifecycle—enforcing security, transforming data, or throttling traffic. But as organizations scale, managing these policies across hundreds of APIs and operations becomes a labyrinth of duplicated code, hidden configurations, and maintenance nightmares.
Introduction:
A policy fragmentation, a game-changing feature in APIM that re-imagines policy management by breaking monolithic configurations into modular, reusable components. Imagine defining a rate-limiting rule once and applying it seamlessly across all APIs, or centralizing authentication logic to ensure consistency while eliminating redundancy. Policy fragments not only streamline development but also turn maintenance into a single-step process—fix a fragment once, and every API referencing it inherits the update.
When you work with Azure API Management on a regular basis, you probably are familiar with policies. Policies allow you to perform actions or adjustments on the incoming request before it’s sent to the backend API, or adjust the response before returning to the caller.
Policies can be applied on various levels, so called scopes, and each lower level can inherit the policy of a higher level.
- Global level => executed for all APIs
- Product level => executed for all APIs under a product
- API level => executed for all operations under an API
- Operation level => executed for this single operation
What is Fragmentation in APIM?
Fragmentation in Azure API Management (APIM) refers to the ability to break down API policies into smaller, reusable components called policy fragments. These fragments can then be applied across multiple APIs or operations within an API Management instance. Each policy fragment typically consists of one or more policy elements that define a set of instructions to be executed within a specific stage of the API request-response lifecycle (inbound, outbound, backend, on-error).
Fragments promote reusability by allowing you to define common sets of policies that can be shared and applied across different APIs or operations
Fragmentation improves development efficiency by eliminating the need to duplicate policy configurations across APIs. Changes made to a policy fragment propagate to all APIs where it’s applied, reducing maintenance efforts
Why Fragmentation required for policy creation?
The main problems with policies always have been maintenance and reuse. Policy code is quite hidden within the portal (especially with so many scope levels where it can reside), so it’s hard to see where a policy is used. When a certain piece of policy is used in multiple places, it’s even harder to keep track where they’re used and keeping them consistent. Bug fixing is difficult and cumbersome, as you need to find out all the places where you need to fix it.
To overcome the above problem, Microsoft introduced the apim Fragmentation.
Benefits of using policy fragments
There are several benefits to using policy fragments in your Azure API Management policies:
Reusability : Policy fragments allow you to create reusable code snippets that can be used in multiple policies. This promotes code reuse and reduces the amount of code you need to maintain.
Modularity : Policy fragments promote modularity by allowing you to create self-contained code snippets that can be added to a policy when needed. This makes it easier to read and understand policies, as well as test and debug them.
Maintainability : Policy fragments make policies more maintainable by allowing you to make changes to the code in a single place, rather than having to update the same code in multiple policies.
Readability : Making it easier for other developers to understand and review your code. With modular and reusable fragments, it’s easier to spot mistakes and ensure consistency across policies.
Use case:
Consider, your organization has three APIs: PaymentAPI, UserAPI, and InventoryAPI. All APIs need a rate limit of 100 requests per minute per client to prevent abuse. Instead of duplicating the rate-limiting policy in each API’s configuration, you’ll create a reusable policy fragment and apply it centrally.
Let’s consider a simple example of APIM fragmentation for rate limiting, which is a common use case in API management. In this example, we’ll create a policy fragment for rate limiting and apply it to multiple APIs within an API Management instance. For this example we are going to have create policy for controlling the API request.
Understanding the <rate-limit> Policy in Azure API Management
The <rate-limit> policy in Azure API Management (APIM) is a critical tool for controlling API traffic by restricting the number of requests a client can make within a specified time window. This policy helps prevent abuse, manage resource consumption, and ensure fair usage across consumers. Below is a detailed breakdown of its attributes, behavior, and practical use cases for your article.
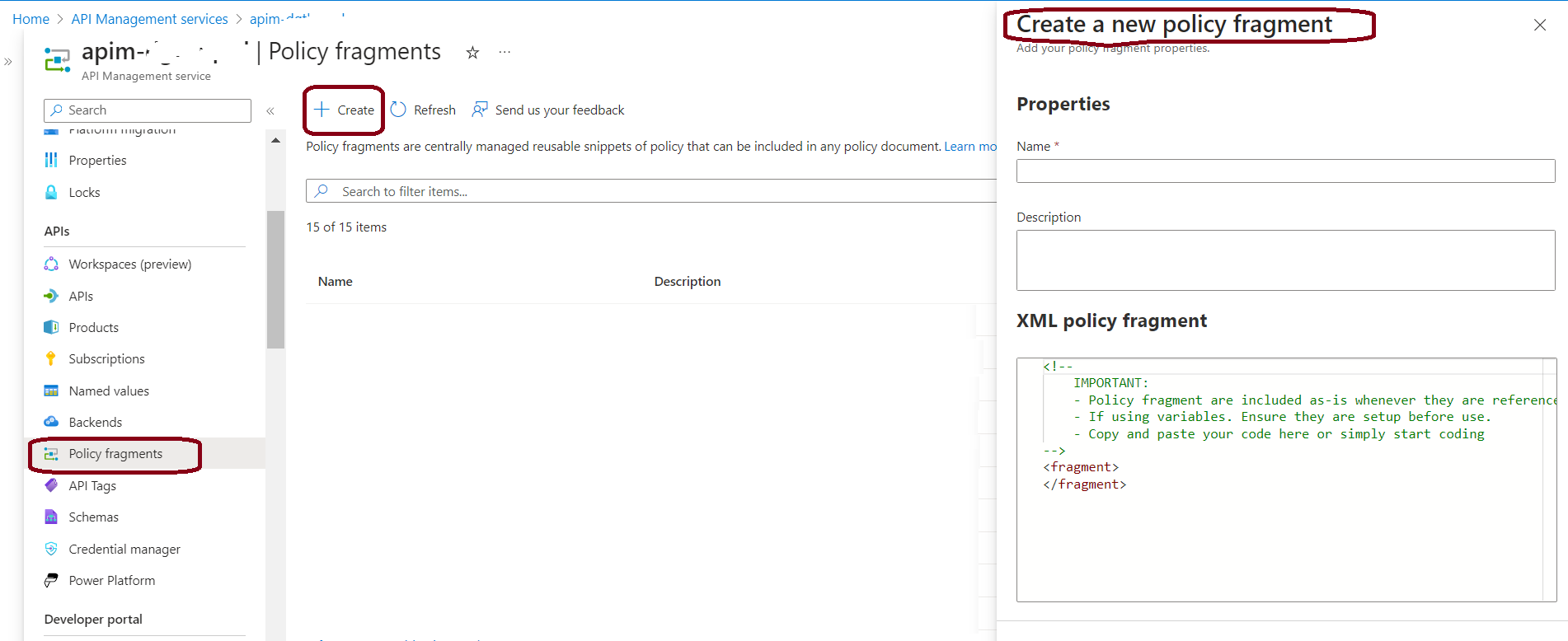
Step: 1 Click & go to “Policy Fragments”
Go to “Policy fragments” in the left menu panel and click create button. You can able to view like below snap.
Step: 2 Enter the properties to create New Fragments
Apply the details, of Name of Fragment, its description and policy like shown below.
[su_highlight background=”#ffffff” color=”#f91355″]rate-limit – The policy in Azure API Management (APIM) enforces a request quota per client to prevent overuse or abuse of your API.[/su_highlight]
<!-- rate_limiting_fragment.xml --> <rate-limit calls="100" renewal-period="60" />
Step: 3 Finally click create button
You can able to see, our Fragment is created and there is 0 reference, means it is yet to apply to any policy.
How to add the fragment in the policy
These fragments can be included in the policy of individual APIs or operations using the <include> element, allowing for modular and reusable policy configurations. If you click on the created fragments, you can able to see the view, how to include this fragment in the policy (pls refer the last snap mentioned in the post).
## Add below line in the policy to include the Fragment <include-fragment fragment-id="fragment_rate_limit" />
Edit Fragment for update:
You can click on Policy editor to open the policy to edit/update and save
Best Practices
- Naming Conventions: Prefix fragments with fragment_ for easy identification.
- Documentation: Add <description> tags in fragments to clarify usage.
- Reference Tracking: Use the References column in the Policy fragments list to identify impacted APIs.
By leveraging policy fragments, APIM becomes a scalable, maintainable solution for enterprise-grade API governance.
Summary
Azure API Management (APIM) policies enable customization of request/response behavior at four scopes: Global, Product, API, and Operation. However, maintaining and reusing policies across these scopes can be challenging due to hidden configurations and duplication. Policy Fragmentation addresses this by breaking policies into reusable XML components (fragments). These fragments centralize common logic (e.g., rate limiting, authentication) and are included via <include-fragment>, ensuring consistency, reducing redundancy, and simplifying updates. For example, a rate-limiting fragment can be applied across multiple APIs, and changes propagate automatically. Fragments improve maintainability, enforce standardization, and streamline debugging.